Here’s a Rest Day Ruminations post. Thank you to my lovely paying subscribers who make some of the posts open to all, as with this one.
2FA Improperly Implemented
Nowadays there are a lot of systems and websites that we use. Many of them require an account. That leads to access data we must manage.
In many cases, a username and password is sufficient to access an online resource. It is certainly the simplest system (both for the end user, and the service provider), and one we are all familiar with.
In recent years there has been a move to add extra security, especially for important accounts. It might not matter so much if someone got access to my Itch.io account, where they could then download games I got for free, or they could buy new games (using their own money!) until I realised what was happening and locked them out. It might be a big problem if they got access to my bank account and transferred everything out (good luck with that, I don’t think you can transfer moths and dust electronically, but you get the idea.) This extra layer of security is often optional for the end user, but not always.
The main system adopted is known as Two-Factor Authentication (2FA), two-tier authentication, two-step authentication, or Multi-Factor Authentication (MFA). I’ll use the term 2FA from now on.
The idea here is that access requires both something you know (a username and password, for example) AND an additional factor of something you have access to. (Ideally, something no one else can access easily.) A code can be sent to that second factor (the code is sometimes called an OTP – a One Time Passcode), which also has to be entered in order to log in to the service. That way, if a baddie managed to steal your username and password, they still wouldn’t be able to access your account, because they wouldn’t be able to receive the passcode sent to your device.
These are some of the options for 2FA.
Landline. This is one of the options the UK government uses for access to the HMRC site, for when I do my tax return. I enter my username and password into the HMRC site, the landline phone rings, I answer it, a code is read out by a computer; I type that into the login page, and can then begin the painful bit of paying taxes.
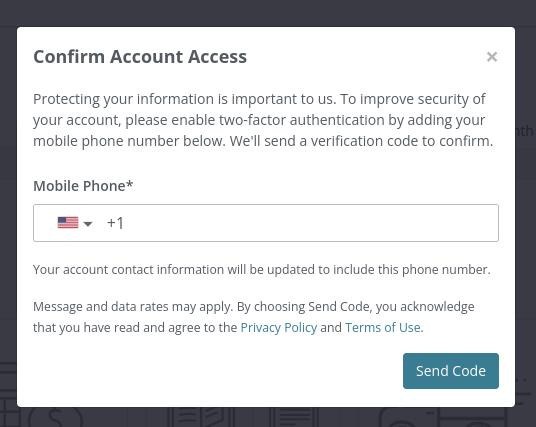
Mobile phone. This can either work as above (automated voice call giving a code) or the code can be sent by text/SMS. This is a popular option, but note that mobile phones can be stolen, cracked and hacked, whereas a landline can’t be stolen or used anywhere except in your house, so in many cases a landline is a more secure option.
Email. If I log in to Steam or Carrd from a new computer I get an email with a passcode, and can copy and paste it to log in.
App/software. Some kind of authentication app generating a code which can be entered. Unfortunately, they are often only available on some computers and platforms, not all; they may be created by companies you prefer to avoid (e.g. Apple, Google, Microsoft); and there may be security risks related to installing the software. If there was an open-source authenticator available on every platform (Linux, Windows, OSX, Android etc) and which all sites and services allowed as a security option, then that would be useful, but it isn’t the case. Also, most apps are mobile phone based, so are redundant when the phone could do 2FA already via text.
Hardware security key. A physical device, probably USB, that plugs into a PC.
Although it isn’t technically 2FA, it has been standard for many services to have additional passcodes. So my bank account didn’t just have a username and password, it had a separate PIN number, and I could also be asked to provide answers to questions like a memorable name or date. That system works well as an easy-to-implement second layer of verification.
None of the options are perfect, they all have pros and cons. Not all of them are available to all people, all of the time. As an example, I hate mobile phones. The only 2FA options that work for me are landline or email. In fact, my email is more secure than most people’s. Instead of some generic gmail (or whatever) address, I have my own domain, and control the security so that you pretty much need to be in my house and log in to my (two-way firewalled) desktop PC to access it.
None of the options are perfect. And none of them work for everyone, all the time, therefore effective implementation of 2FA would offer at least three options for users: landline, mobile phone (call, text or app), and email. I call this “professional 2FA”. Professional 2FA adds an extra layer of security, without excluding or upsetting any of your users, or creating exceptional barriers to access (known as digital exclusion).
Unfortunately, many companies and IT people interpret 2FA narrowly as mobile phone-only, and only implement that single option. They don’t bother to set up any other options, or worry about the people who will now have problems accessing the service, so that security stops being the system that keeps unwanted users out: it becomes the system that puts barriers in place of legitimate users. They are either lazy (can't be bothered offering alternatives), or inept (don't think to offer alternatives for when mobile phones are inappropriate). I call this “lazy 2FA” or “shit 2FA”.
“But, Karl, the IT people are the experts.”
Long ago I realised that many people labelled as experts have the same myopias and prejudices as anyone else, often basing things around their own preferences and prejudices. They’re human, not robots. Likewise they can be lazy (“Why implement all the options and be helpful, when we could just implement one option and leave the poor customer services staff to deal with the backlash?”) or misinterpret guidance (e.g. guidance on good 2FA includes options to make sure legitimate users can access the service). Slapdash implementation means you get slapdash 2FA).
Here’s a story. I once worked on an IT helpdesk in a big organisation. The experts in charge of IT security decided that passwords shouldn’t be crackable, so “best practice” involved strict rules for the creation of passwords. No real words, in any language, forwards or backwards; requirements to use symbols and numbers (but not in place of letters – kj!5l1aw would get rejected because it included the text string “walls” backwards). It immediately led to a huge amount of extra work creating and resetting passwords at helpdesks because passwords were no longer easy to remember. I’d be sat there and almost everything the user typed in would be rejected as it contained some word from French or German or Welsh somewhere within it. Because – guess what? - most long strings of text will match up with short words in some language forwards or backwards, especially when symbols are used as letter replacements. Cue very angry users, and a waste of staff time as we went through suggesting different ways of thinking of phrases and just taking the first letter of each word (which still often got rejected).
The end result? No one could remember the passwords so they got written on sticky notes, scraps of paper tucked into a book, and in diaries. Even more so because the other “good practice” was to change passwords often, meaning a new one every six months, going through all this again. People were always forgetting them, and since “good practice” meant staff couldn’t retrieve the passwords for anyone, we then had to go through the process to create another. I was forever finding slips of paper with people’s passwords on, making a mockery of good practice.
The point is, when experts adopt good practice, the end result is often something that gets in the way of doing the job the system is meant to enable in the first place.
Another example, more recent. I have an employer that uses a 2FA system. Industry-standard, Microsoft. Except it is shit. Even when I follow the procedures, it doesn’t work most of the time. And so I can’t access email or the files I need to do my job. (Another example of why I recommend people ditch Microsoft!)
Back to mobile phones.
Badly implemented 2FA (where only mobile phones are allowed) is very much like that. So when the British Library implemented 2FA and refused to allow email as an option, telling me their “chosen method for automated authentication was implemented on the advice of our IT security team” I groaned. Ah. The experts in the IT security team. That’s why I can no longer amend my Public Lending Right (PLR) bank account without scheduling a video chat with a member of British Library staff so they can ask me questions and scrutinise my face, invading my privacy and wasting time and money.
I’m going to focus on the lazy implementation of the mobile phones option, since I think it’s a curse on society.
I have some elderly friends who live in the highlands of Scotland. Not too far from a city, but it’s still remote. There is no mobile phone signal in their house. When some service forces them to use mobile-based 2FA, they don’t receive the code. The only way they can log in is to check the phone is charged (since it is mostly turned off in a drawer, and only used if they go into town or travelling), get kitted up, and head out, then trudge up a big hill. It could be dark, icy, chucking it down. They might be ill. Tough. It’s inconvenient, unpleasant, time consuming, puts them at risk, and (to cap it all) sometimes they get back home and the code has expired, requiring doing the process all over again. The frustrating thing is, if the code had been sent by landline or email, it would have been no problem at all. They have a phone and broadband.
I have another friend who owns a mobile phone, but it’s only for emergencies, friends and family. He never gives the number out to anyone else, including companies that ask for it. If that phone rings, he knows it is truly important, not just one of endless distracting notifications and spam calls. In fact, he told me he has never received a spam call, and puts it down to the fact that he doesn’t trust any organisation with that number. Of course, every single site that asks for your details will say they don’t pass your details on, but some of them must be lying. We all know that as soon as we start handing over our email address and phone number, we start to get more and more spam. Plus, even the best-intentioned companies get hacked, and data stolen (which happens to big companies and small; and many of them try to hide the fact if they can). My friend cares a lot about his privacy, and refuses (quite rightly) to give in when companies keep demanding access to his personal hotline.
Final story!
“What’s Karl’s problem? Why would anyone not want to own a mobile phone! They’re great! Ping ping, hold on a mo, that’s another notification …”
I’m not a Luddite. I use Linux. I used to be an e-learning advisor for JISC. I was one of the first to own a smartphone, and would examine how it could be used to enhance teaching and learning (along with interactive whiteboards, voting systems, blogs, social media, VLEs and so on). But I soon realised that technology just for the sake of it is pointless.
And I have my personal, spiritual beliefs. As a Pagan I want to be able to enjoy the beauty and peace of nature, not stare at a tiny screen. I want to feel free from interruptions and constant nagging that comes with notifications and apps.
As someone concerned about privacy I hate the endless tracking of smartphones and their apps. I dislike big tech companies for similar reasons to why I avoid supermarkets and big chains in favour of local independent shops such as the baker, the greengrocer, the independent cafe, charity shops, small bookshops; why I favour paying in cash rather than digitally, where the shop loses a cut of the money to the payment providers (whilst enabling every transaction to be tracked).
As such I have been spending years closing accounts to cut Amazon, Google, Microsoft, Apple, Facebook and the rest out of my life. I care about the environment, and the huge damage done by the wasteful culture of constant upgrades and replacement of gadgets, accelerated obsolescence, advertising and consumer culture trying to scare people into thinking they always need the latest whatever otherwise they’re worth less as a person.
A life tethered to devices (voluntarily, no less) seems like less of a good life to me, and more like a dystopia. So I react against it. You may think I’m mad and disagree, but I’m not telling anyone else what to do, I’m just explaining my preferences.
Okay, back on topic. When there is a poor implementation of 2FA (“lazy 2FA”) that insists everyone owns a personal mobile phone and must share the number and use that device as a second factor, with no other options, then it excludes or creates barriers for people who fall into one or more of these categories (which apply to all people at some time, and some people all the time):
people who don't own a mobile phone (through choice or any other reason);
people who don’t have access to their mobile phone (lost, broken, misplaced, stolen; or even while they wait for a replacement SIM card to be posted);
people living in or visiting an area with no mobile phone signal;
people who own a mobile phone but only use it for emergencies, or only give the number to friends and family, and don't want to give the number to anyone else (quite rightly!).
Sometimes the most vulnerable people fall into those categories, those already facing marginalisation (for example the rural and isolated, poor, digitally excluded) – the people in most need of access to services. And instead of enabling that, lazy mobile-only 2FA creates digital exclusion and further barriers for the vulnerable. It’s for these cases (as well as true good practice) that – whether you own a mobile phone or not – when a company demands your number for 2FA, you could insist on making sure they also offer other options to cover everyone: landline and email. You’ll be doing a service for everyone whose life doesn’t centre around mobile phones.
The oversight comes about because an IT security team has a single focus: IT security. But then issues like digital exclusion are not part of their remit (plus they don't even consider them because the IT people use tech all the time) and so important things get sidelined by the single focus. Hence “our experts advised this” just translates as “this system was designed by people with such specialised knowledge that they no longer have the big picture”. That is ever the problem with specialisation and the fragmentation of knowledge, and the danger of leaving policy to self-proclaimed experts. It's basic stuff, and yet even tech people and security people often seem unable to comprehend it.
Lastly on this topic, there is a fundamental extra problem with 2FA. Once an identity is tied to an extra item, everything is hunky dory whilst access is available. This is how the 2FA implementers like to see things: everyone connected, all the time, with mobile signals and fast networks, where nothing breaks or gets lost.
That’s not the real world. Phones break. They get lost, or stolen. People replace them or buy new ones. People pass through areas (or live in them) that have no signal. Email goes down, and email addresses change. People move house, landline numbers change. And so on.
Suddenly we have a rigmarole of having to plan for change. No, you can’t just get a new phone number. First you have to contact every company that has the old one and uses it for 2FA (you do have a list of them, don’t you?) You have to access your account, change the number to a new one, use the old phone to authenticate, then the new one to do so. (Try explaining all that to your gran.) Even when things go perfectly it is a lot of hassle and time for multiple accounts; every year that goes by, this will get even more complicated.
But when your phone breaks or goes missing, you can’t do that. If you don’t have a list of every 2FA service you use, you can’t do that. Suddenly – as with every case above where access to the second factor is impossible – 2FA doesn’t work.
Security is always a balance. The more the security, the more hassles for people, and the greater the chance of being locked out.
So what do you do in those cases?
You have to contact that service. To find a customer support number or link or email for Facebook or Google or whatever.
Good luck with that. Most companies make savings by outsourcing or removing front-facing support. The number of sites in the last few years where I can’t find a contact email or phone number has grown hugely. Often you’re pushed into a live chat with a bot that doesn’t understand anything and can’t fix anything.
Then, if you do get to a human, you face an even bigger problem, exacerbated by 2FA.
Without that second factor, they have no way of knowing if you are really the person you say you are, and really have lost or changed your phone/email; or if you are a criminal pretending you are the user, in an attempt to get the second factor changed to one the criminal owns.
Both scenarios look exactly the same: person saying they can’t log in because they can’t get the 2FA passcode.
So what do the companies do?
They can’t ask for the username and password. If that was enough to fix things and access the account, then there was no point in 2FA in the first place.
So they could ask for extra details. But what? Your name and address? The criminal would probably have those. And again, if they were enough to prove who you were, then why not just use those as login details?
Maybe they’ll ask questions about your activity. I’ve had that with my bank. “Tell me your last few bank transactions.”
At which point my mind goes blank, and I realise I’m not sure what payments might have gone out unless I can open my transaction document on my computer, and did I use this account or the joint account to buy a bar of chocolate?, and has a royalty payment gone in or was that last week?, and I give vague ideas of when I used my account and for what, but it sounds very suspicious, and I don’t get all the transactions right, and I tell them that if I was able to give them every transaction correctly then it would only prove I am not Karl Drinkwater, and then they put me through to the fraud department and I have to do it all over again.
Organisations are very cagey about what they do in these circumstances when you ask them. They say they can’t tell you, because of “security”. The truth is that it’s a massive weak spot in 2FA, because suddenly the whole thing that is meant to make an account secure is not working, and it is replaced with a time-consuming, insecure, annoying process.
As mentioned above, when The British Library implemented it, I could no longer amend my bank account details in their PLR system unless I had a video chat with them. “There is also the option for users to complete an authentication check via video call,” they told me.
Even then, they wouldn’t know the difference between me and a criminal, since the person at the British Library end has no idea what I look like and has never met me before.
I wasn’t satisfied with the British Library’s response to how a video chat would act as proof; their response ended with: “We are not able divulge all the details of our security checks and processes."
They never answered my question about how a video chat would confirm my identity, rather than just being an extra barrier. That anything they might ask me, if acceptable as proof, could just as easily be an additional security question without all the hoo-haw. Perhaps they would base “proof” on how the authors look, and go Googling for pictures of people in advance? As well as that being borderline privacy invasion, many authors use pen names and sometimes licensed photos for the pen name that aren't the real person, so it doesn't prove anything. Also, some people don't like being scrutinised visually by strangers.
At heart, a video chat can’t be used to prove the identity of a customer who only exists as a few fields in a database.
And since that option is awful, that leads to organisations falling back on another, also-awful one (and potentially more dangerous). It’s the one that Amazon, Facebook, Paypal and so on often resort to.
They ask you to scan in and send them a copy of some form of official ID. Passport, driving licence, birth certificate. They promise you the process is secure. Yes, a human will have access to check it, but they’re all trustworthy, not minimum-wage staff in a role with high turnover who are faced with checking thousands of documents every day until their eyes go blurry. They’ll probably want to keep the copy stored, in case of future authentication issues, though they might not admit that.
Do you know what the biggest security risk is, when it comes to identity theft? Criminals getting hold of scans of your documents. Suddenly they have all the things they need to impersonate you. To create new accounts. To gain access to your other accounts. Every single day big companies are being hacked. Data is being stolen. Not long ago the British Library sent me an email telling me they’d been hacked (though they kept quiet about it for over a month) and – you guessed it – personal data had been stolen. Including this kind of thing, it seems. So scans of passports and so on are key targets for criminals. Only a security idiot would insist on these documents being scanned and sent to companies in other countries.
Once copies of your official ID are out of your hands, you have no control over them. And, unlike an email account or phone number, where you can easily just get a new one and invalidate the old, that doesn’t apply to birth certificates, passports, driving licences. Once someone has copies of them, they have the foundations for proving they are you, impersonating you online, accessing accounts they shouldn’t, and much more.
So 2FA adds extra security in some ways, but becomes problematic in others. Overall I think it can be a net gain, but only if implemented properly in a non-discriminatory way: there has to be a choice of systems for the user, so they can pick the one that works for them, that they have access to. So there has to be a choice between mobile phone, email, and landline phone, at a minimum. (And ideally the option not to use 2FA at all, if all the options given are problematic: I already discussed the “secondary login” idea above, in terms of PIN numbers and memorable names.)
And 2FA should only be implemented when there is a clear policy on what will happen if the 2FA device isn’t available to you (and that must involve a help service where you can easily speak to a human who can sort out your access via another route, and which doesn’t involve sharing highly sensitive documents).
In 2023 when Ingram Spark implemented Lazy 2FA, and since then every time I log in I get a nag box telling me to give them a nonexistent mobile phone number, The end result of a lazy implementation. Nagging me every time I log in won't magically create the mobile phone numbers they want to gather, it just pisses customers off.
(Luckily Bookvault, Draft2Digital, Card, Gumroad and Lulu don't force you to provide a phone number, because they have a good customer focus and don't want to exclude people.)
Just as IngramSpark nags me for a mobile phone number, you find other companies doing that. I had all sorts of problems with the Cooperative Bank – they do actually have an option to use email for 2FA but didn’t mention it anywhere in the emails they sent customers. The text of their messages specifically said we had to use mobile phones. Even after I had pointed this out multiple times (and they apologised for misleading people) they still continued to try and scare customers into giving them mobile phone numbers by saying it was a requirement for shopping online. A blatant lie. You see, companies don’t like dealing with the real world. They want to pressure people into doing the same thing. They want to adopt the lazy options, and lazy 2FA wherever possible. They want to gather and store more personal data about you (which, coincidentally, is how advertising companies track you and connect up data to create profiles so they can hit you with even more advertising).
In June 2021 I contacted the UK Financial Conduct Authority (FCA) about this topic. The FCA give guidance to UK organisations, and they said: “It is necessary for a firm to provide different methods of authentication, for example, to take into account the fact that not all service users will possess a mobile phone.” Making a mobile phone a requirement (rather than an option) is digital exclusion, and is a serious issue.
At its core, 2FA/MFA isn't bad. If it is implemented well, in a way that doesn't exclude anyone. All that is required is to offer options, so that people can choose the system that works best for them.
If you want to do a good deed, as well reinforcing good practice, then – whether you own a mobile phone or not – whenever a company demands your number for 2FA, check that they also offer other options to cover everyone: landline and email. You’ll be doing a service for everyone whose life doesn’t centre around mobile phones.
If you made it this far, you deserve a medal, or a free ebook or something. Send me an email by replying to this. :-)



I agree with you. As my husband and I have been trying to merge certain accounts, the 2-f always goes to his cell phone making it difficult if he's not in the house.. I handle our tech issues and I have all the passwords, etc., stored in my phone and printed out in our "binder" of important documents, still things slip. I don't like the 2-f and I wish one could opt-out. I feel for folks in areas without cell service or do not have cells, especially our elderly populations who don't have email, etc. My husband at (60-ish) has no social media and barely uses email.
Technology that causes more bumps than merges is definitely a burden.